Trusted Platform Module (TPM)
2017-05-19
Outline
- Why?
- What?
- How?
- Issues
Why does TPM exist?
Why does TPM exist?
[…] if the attacker can control the machine, we must not use that machine to handle our cryptography. If we cannottrust the host, we must look elsewhere for something else to which we canentrust our keys . […]
Handbook of Information Security - Volume 3
Why does TPM exist?
Trust
"Assured reliance on the character,ability , strength ortruth of someone orsomething ."
Why does TPM exist? — Trust
Why does TPM exist? — Trust
Why does TPM exist? — Trust
Why does TPM exist? — Trusting computers
But can we trust computers?

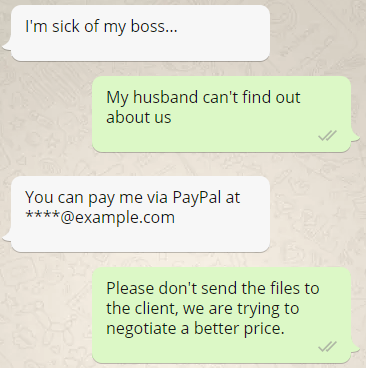
Why does TPM exist? — Trusting computers
Can we trust computers?
No, not entirely — human product after all
[…] if the attacker can control the machine, we must not use that machine to handle our cryptography. […]
Handbook of Information Security - Volume 3
Why does TPM exist? — Trusting computers
According to darkreading.com, in 2016:
- 4149 data breaches
- 4200 million records exposed
- Up from 1000 million in 2013!
And 2017 is already not looking good:
- WannaCry
- GoogleDocs Phishing
- US + France elections
- Coming soon: Germany elections
What is TPM?
What is TPM?
[…] The idea of ahardware security model is to separate out the cryptographic key storage and processing functions into adevice that we do trust . […]
Handbook of Information Security - Volume 3
What is TPM?
A Trusted Platform Module (TPM) is:
[…] a hardware component that uses its own internal firmware and logic circuits for processing instructions. […]
What is TPM?
Brief history of TPM
- Hardware module specification
- Developer: Trusted Computing Group (TCG)
- First version: 1.1b (2003)
- Common version: 1.2 (2009)
- Latest version: 2.0 (2014)
- Supported by Windows and Linux
- Standarised through ISO and IEC
What is TPM?
Features of TPM
- Random Number Generator
- Generate and manage keys
- De/encryption and signing
- Monotonic counters
Boot counter and timer - Small Non Volatile (NV)RAM
- Reads computer state from the bus
- Platform Configuration Registers (PCR's). Software state
What is TPM?
Crypto TPM facts
- Public, accepted Crypto standards
- v2.0 requires SHA-1, SHA-256, RSA, ECC, HMAC, AES
Many optional algorithms - v1.1b and v1.2 assume internal usage of SHA-1
v2.0 allows other hash algorithms (algorithm agility) - Algorithm agility in v2.0 implies larger hash sizes
Solution: e.g. AES(Data) and RSA(AES_KEY) - v2.0 supports stream encryption
How does TPM work?
How does TPM work?
[…] Such a device should have asimple andstrict ly definedinterface , and if physical access is an issue, it should alsoresist tampering . […]
Handbook of Information Security - Volume 3
How does TPM work?
TPM 2.0 hierarchies
Software
(Firmware,
OS, ...)
(Firmware,
OS, ...)
TPM
Platform
Storage
Endorsement
How does TPM work?
TPM 2.0 Encryption
Software
(Firmware,
OS, ...)
(Firmware,
OS, ...)
GenKey(algorithms,
size, policy, type,
unique data) →
size, policy, type,
unique data) →
← Key id
Encrypt(algorithms,
key id, data) →
key id, data) →
← Encrypted data
TPM
Platform
Storage
Endorsement
How does TPM work?
TPM 2.0 Decryption
Software
(Firmware,
OS, ...)
(Firmware,
OS, ...)
GenKey(algorithms,
size, policy, type,
unique data) →
size, policy, type,
unique data) →
← Key id
Decrypt(algorithms,
key id,
encrypted data) →
key id,
encrypted data) →
← Data
TPM
Platform
Storage
Endorsement
How does TPM work?
TPM 2.0 Policies
Policies define key usage. Can be a very complex combination of:
- Password
- Biometrics
- HMAC
- PCRs (state)
- Boot counter or timer
How does TPM work? — BitLocker
BitLocker encryption
Data
Full volume encryption Key
How does TPM work? — BitLocker
BitLocker key protectors
- Clear key
- Startup key only
- Recovery key
- Recovery password + salt
- TPM key + startup key
- TPM key + PIN
- TPM-only key
How does TPM work? — BitLocker
BitLocker
Load BitLocker
Read metadata
GenKey(policy,
unique data) →
unique data) →
← Key id
Decrypt(key id,
encrypted data) →
encrypted data) →
← Data
Protector Key = Data + PIN
TPM
Platform
Storage
Endorsement
Issues with TPM
Issues with TPM
Issues with TPM
- TPM manages keys, does not stop code from running
- Endorsement hierarchy raises privacy issues
- Digital Rights Management with TPM
Questions?
Thank you!
Sources can be found online after this slide
Sources
Picture and quote sources can be found in the respective slide.
Researched material:
- Will Arthur et al. A practical guide to TPM 2.0 : using the trusted platform module in the new age of security. New York : ApressOpen, 2015. ISBN: 9781430265832.
- Roger R. Dube. Hardware-based computer security techniques to defeat hackers : from biometrics to quantum cryptography. Hoboken, NJ : Wiley, 2008. ISBN: 9780470193396.
- Norbert Pohlmann. Trusted Computing : ein Weg zu neuen IT-Sicherheitsarchitekturen. 1. Aufl. Wiesbaden : Vieweg, 2008. ISBN: 9783834803092.
Sources
- Peter Stavroulakis. Handbook of information and communication security. Berlin ; , Heidelberg : Springer, 2010. ISBN: 9783642041167.
- Sven Türpe et al. “Attacking the BitLocker Boot Process”. In: Proceedings of the 2Nd International Conference on Trusted Computing. Trust ’09. Oxford, UK: Springer-Verlag, 2009, pp. 183–196. ISBN: 978-3-642-00586-2.
- Sasu Tarkoma. Mobile middleware : architecture, patterns and practice. 1. ed. Chichester : Wiley, 2009. ISBN: 9780470740736.
Sources
- Trusted Computing Group. TPM Main Specification. Version Revision 116. [Online; accessed 11-May-2017]. TCG. 2011.
- Trusted Computing Group. TPM 2.0 Library Specification. Version Revision 01.38. [Online; accessed 11-May-2017]. TCG. 2014.
- Handbook of information security. Vol. 3, Threats, vulnerabilities, prevention, detection and management. Hoboken, NJ :Wiley, 2006. ISBN: 9780471648321.
- Jiun Yi Yap and Allan Tomlinson. “Threat Model of a Scenario Based on Trusted Platform Module 2.0 Specification”. In: WASH. 2013.